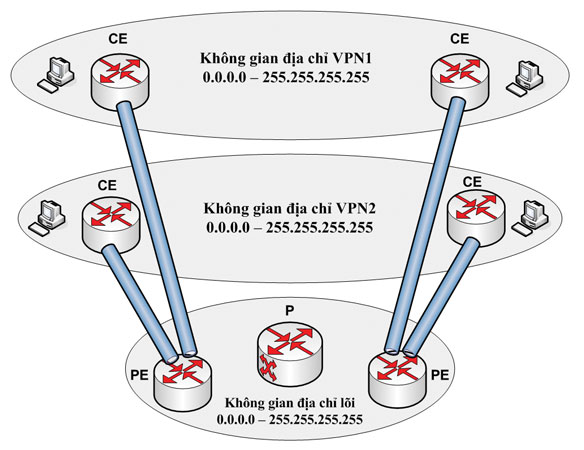
Tích hợp thuật toán mật mã mới trong mạng riêng ảo OpenSwan
Abstract- This paper presents a method to integrate a new cryptography algorithm into the open source system OpenSwan for building a virtual private network (VPN). The OpenSwan plays an important role in confidential data in the virtual private network, specially for building a cloud computing system. Although there are several cryptography algorithms installed in OpenSwan, users need to use the other new algorithm in some typical cases for protecting their sensitive data so the studying to install a new cryptography algorithm in OpenSwan is necessary and useful. Based on analyzing priciple operating and source code of system, we proposed the model used to replace a crypto algorithm in OpenSwan. Experiment results show that the proposed method is easy and good performance.
|
Tài liệu tham khảo [1]. “Architecture", Journal of Advances in Computer Networks, Vol. 2, No. 4, 2014. [2]. M. Fahandezh, M. Bondy, and S. Erfani, “A framework for implementing IPSec functional architecture”, in Proc. Canadian Conference on Electrical and Computer Engineering, pp. 71-76. [3]. D. Maughan, B. Patrick, and M. Schertler, “Internet Security Association and Key Management Protocol (ISAKMP)”, Internet-Draft, IPSEC WG, 1996 (File: draft-ietf-ipsec-isakmp-06.txt) [4]. HK. Orman, “The OAKLEY Key Determination Protocol”, Internet-Draft, IPSEC WG, 1996 (File: draft-ietf-ipsec-oakley-01.txt). [5]. A. Aziz, T. Markson, and H. Prafullchandra, “Simple Key-Management For Internet Protocols (SKIP)”, Internet-Draft, IPSEC WG, 1996 (File: draft-ietf-ipsec-skip-07.txt). [6]. P. Karn and WA. Simpson, “The Photuris Session Key Management Protocol”, Internet-Draft, IPSEC WG, 1996 (File: draft-ietf-ipsec-photuris-11.txt). [7]. H. Krawczyk, “SKEME: A Versatile Secure Key Exchange Mechanism for Internet” in Proceedings of SNDSS ’96, IEEE (1996) pp.114-127. [8]. Robert Love, “Linux Kernel Development”, Addison-Wesley Professional, 3rd Edition, pp. 440, 2010 (0672329468). [9]. Daniel P. Bovet, “Understanding the Linux Kernel”, O'Reilly Media, 3rd Edition, pp. 944, 2005. [10]. Wolfgang Mauerer, “Professional Linux Kernel Architecture”, Wrox, 1st Edition, pp. 1368, 2008 (ISBN-13: 978-0470343432). [11]. James Morris, “The Linux Kernel Cryptographic API”, Linux Journal, 2003. [12]. Abdulellah A. Alsaheel and Ahmad S. Almogren, “A Powerful IPSec Multi-Tunnels” . [13]. Jean-Luc Cooke and David Bryson, “Strong Cryptography in the Linux Kernel”, Discussion of the past, present, and future of strong cryptography in the Linux kernel, 2003. [14]. Lei Gong, “A new framework of cryptography virtio driver”, Huawei Technologies Co., LTD., pp. 1-5, 2005. [15]. Rami Rosen, “Linux Kernel Networking: Implementation and Theory”,A press, p. 636, 2013. [16]. Stephan Mueller and Marek Vasut, “Linux Kernel |
Nguyễn Như Tuấn, Phạm Văn Hưởng, Phạm Quốc Hoàng